
Abstract: SCADA system is widely used in many fields, such as data acquisition, monitoring and control, process control and so on. For a long time, many engineers and managers believe that SCADA system is a relatively isolated physical isolation system with strong access control and relatively safe. However, with the development of network technology, communication technology and computer technology, SCADA system has gradually developed into an open and transparent standard system, resulting in the reduction of system security. Aiming at the current Open SCADA system, this paper introduces the system composition and network structure characteristics of the system, analyzes the possible security risks of the system, and puts forward a hierarchical "defense circle" security strategy. The strategy implements specific security protection measures from two aspects: enterprise network and SCADA network. Through the reasonable configuration of each layer in the "defense circle", the security of SCADA system can be effectively guaranteed.
1 Introduction
SCADA system is widely used in many fields, such as data acquisition, monitoring and control, process control and so on. In the initial stage of the development and application of SCADA system, the system is a relatively isolated physical isolation system with strong access control and is relatively safe. However, with the development of network technology, communication technology and computer technology, SCADA system has gradually developed into an open and transparent standard system, resulting in the reduction of the security of the system. With the acceleration of enterprise informatization, the security of SCADA system also El increasingly highlights its important strategic significance.
2 SCADA system
SCADA (supervisory control and data acquisition) system, namely data acquisition and monitoring control system, is a computer-based production process control and dispatching automation system 1J. It can monitor and control the on-site operation equipment to realize various functions such as data acquisition, equipment control, measurement, parameter adjustment and various signal alarms. SCADA system is the most widely used and mature technology in power system. As the most important subsystem of energy management system (EMS), it has the advantages of complete information, improving efficiency, correctly mastering the system operation state, accelerating decision-making, and helping to quickly diagnose the system fault state. Now it has become an indispensable tool for power dispatching. 4.
SCADA has been applied in railway electrification telecontrol system earlier, which plays a great role in ensuring the safe and reliable power supply of electrified railway and improving the dispatching management level of railway transportation. SCADA plays an important role in petroleum pipeline engineering. It systematically manages the sequence control and transmission of petroleum pipeline, equipment monitoring, data synchronous transmission record, and monitors the operation status of the pipeline and each station control system. In addition to this basic function, the current SCADA pipeline system also has new functions such as leakage detection, system simulation and water hammer advance protection.
2.1 composition of SCADA system
SCADA system is generally composed of three parts, including remote terminal unit (RTU) installed in each grass-roots production unit, communication network to realize data transmission between field equipment and master station system, and master station system to provide human-computer interaction interface. Remote terminal equipment is the electronic equipment installed in the remote site, which is used to monitor and measure the sensors and controllers installed in the remote site. RTU generally consists of communication processing unit, switching value acquisition unit, pulse value acquisition unit, analog value acquisition unit, switching value output unit, pulse value output unit and analog value output unit. RTU converts the measured status or signal into a data format that can be sent on the communication media. The function of sending commands from the computer to the central device is also realized. The data communication system is used to realize data transmission between RTU equipment and master station. There are many SCADA communication modes, which can be roughly divided into wired mode and wireless mode. Wired transmission media include optical fiber and cable; Wireless transmission modes include microwave, radio and satellite.
The master station system is usually a network composed of one computer or multiple computers, which adopts UNIX or windows operating system to provide man-machine interface for SCADA system. The huge master station system generally includes communication front-end system, real-time database system, engineer workstation, production scheduling workstation, various monitoring workstations, web server and historical database server. As a SCADA master station system, a large system may have dozens, hundreds of workstations and multiple servers. However, a simple SCADA master station system may have only one computer running a set of software.
2.2 networked SCADA system structure
SCADA system has been closely related to the development of computer technology since its birth. The development of SCADA system has experienced the evolution process from centralized system to distributed system, and then to open network system. The networked SCADA system is closely related to the distributed structure. The main difference is that the networked SCADA system structure is an open system framework, rather than a private system controlled by developers. The adoption of open and standardized protocols can not only share the master station data and function composition between different systems to realize the integrated application of multiple systems, but also realize the distributed function of the system in a wider range. The adoption of open standard protocol eliminates many limitations in the previous SCADA system. In open systems, it becomes easier for users to connect and use peripheral devices (such as monitors, printers, disk drives, etc.). SCADA system is gradually developing into an open and transparent standard system. Figure 1 shows the structure of networked SCADA system.
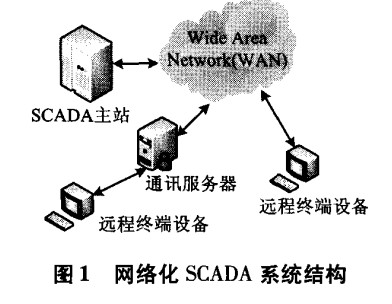
The main progress of networked SCADA system is that it adopts wide area network protocol, such as TCP / IP protocol for communication between master station and control equipment. This enables some master stations mainly responsible for communication with data acquisition equipment to be separated from the master station of SCADA system through Wan. For remote terminal unit equipment, it can also be interconnected with SCADA system and master station through Ethernet communication.
3 potential safety hazards of SCADA system
In recent years, the development trend of SCADA system is mainly reflected in the products based on open standard protocol and more and more cots products. Most SCADA software and hardware developers are using TCP / IP protocol and Ethernet communication technology. The development of these technologies not only makes the system have better compatibility, but also makes the integrated application and system expansion of different systems easier. However, with the standardization of device interface and the application of open system, the requirements for technical content of malicious attacks to successfully implement network control are becoming lower and lower, so the system will face more security risks.
Enterprise intranet is the main way of internal communication. SCADA system has been interconnected with enterprise network, so SCADA system is vulnerable to many attacks based on TCP / IP protocol. Many system managers and system analysts may still believe that their network is independent of the enterprise network and will not be attacked by the outside world. In addition, for RTU, PLC and other equipment, professional communication networks such as radio, telephone line or satellite system are usually used, which often gives the managers of SCADA system a security illusion that their terminal equipment are protected by non corporate network connection, thus reducing the security of the system.
In modern SCADA system, there may be potential safety hazards in many places. Among them, SCADA system host and control room are the most vulnerable to attack. The system host collects the data collected by the remote terminal equipment and transmits it to the background database, which indicates that there is a connection path for the SCADA host to access the database system in the network. Similarly, there must be a connection path to the remote terminal equipment through the SCADA system host in the network. This means that once the enterprise network is attacked, any device or computer system based on TCP / IP protocol may be threatened by security.
Due to the functional requirements of SCADA system, the network is usually connected online and allowed to log in at any time, which makes the possible attacks on the system mainly include the following:
(1) Denial of service (DOS) attack, causing the SCADA server to crash and fail to work normally, resulting in operation failure or system shutdown;
(2) Peek at the keyboard activities of the operator, steal the user name and password, and prepare for further attacks;
(3) Install Trojan horse program to fully control the system and issue operation instructions;
(4) Remote modification of database data, resulting in enterprise data loss;
(5) Steal the company's confidential information or data for use by other competitors, thus making the enterprise lose its competitive advantage;
(6) Change the preset operation or deceive the operator into thinking that the control process is out of control and the system must be shut down or restarted, resulting in data loss to the enterprise;
(7) Maliciously delete system files on the server or damage other device parts in the network.
4 SCADA security defense strategy
In view of the potential safety hazards existing in the SCADA system of enterprises, it is necessary to implement specific safety measures to ensure the safe application and development of the system. Analyze the structure of SCADA system, application policies and regulations of SCADA system, including the appropriate structure of SCADA system, firewall and communication software. In the SCADA system, the security threat faced by the system may come from the Internet attack or from within the SCADA network,
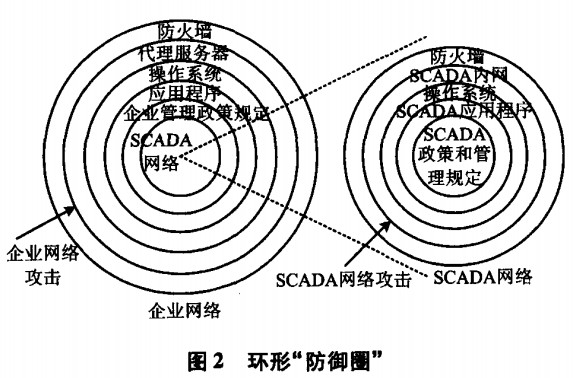
Figure 2 shows a typical defense strategy of enterprise SCADA system, which constitutes a "defense circle" based on hierarchy. In this "defense circle", the protection measures are divided into enterprise network protection and SCADA network protection. Enterprise network protection strategy includes firewall, proxy server, operating system, application and enterprise management policies; SCADA network protection strategy includes firewall, SCADA internal network design, operating system, SCADA application and SCADA management policies and regulations. The network threats of enterprises may come from the Internet or computers in the internal network; The attacks on SCADA network can come from the upstream, such as applications, or from the downstream, such as RTU equipment. Therefore, it is necessary to properly configure the "defense circle" to coordinate the work of all layers in the "defense circle".
4.1 enterprise network security protection
Firewall 1 is a device to help ensure information security. It will allow or restrict the transmission of data according to specific rules. The firewall can be an exclusive hardware or a set of software built on general hardware. Correctly configuring the firewall can play a basic protection purpose, including password security, IP address hiding and file protection. However, in the lack of basic security of the operating system
In case of failure, hackers can directly penetrate the enterprise's internal private network or conduct denial of service attacks.
Proxy server is an important security function. Its work is mainly in the dialogue layer of open system interconnection model, which plays a role similar to firewall. Proxy server is mostly used to connect the Internet and local area network, which is to proxy network users to obtain network information. It is the transit station of network information. However, the proxy server can not eliminate the threat of application layer attack.
Operating system is a program that manages computer hardware and software resources. It is also the core and cornerstone of computer system. The characteristics of the operating system are well known, and the vulnerabilities of the operating system may become the preferred target of hackers, so the patch files of the system should be upgraded in time. Attacks on the application layer of applications, such as buffer overflow, worms, Trojans and malicious ActiveX code, can make anti-virus software lose its protection ability, bypass the firewall and threaten the system security. Policy and management are the basis for the implementation of security strategy. He requires users to improve their basic safety awareness, formulate safety regulations and policies, and require users to implement them in daily operation. Some common regulations, such as not using your birthday or name as a password, the password should not be too simple, at least it should be composed of letters and numbers, and the length should be more than eight characters.
4.2 SCADA network security protection
SCADA firewall. Like the enterprise network, SCADA system and industrial automation network may be attacked by similar hackers. Usually, the SCADA system will also threaten the security of the system due to the use of other internal software tools or the operation of non malicious internal employees. For these reasons, a dedicated firewall for SCADA can be deployed. The SCADA system firewall can isolate the SCADA system network from the enterprise internal network and the Internet, and provide at least two layers of firewall protection between the SCADA system network and the Internet, so as to achieve a higher level of security protection for the SCADA system. SCADA internal network design. The SCADA system network shall use its own network segment to isolate it from the external network. By using IP intelligent conversion and appropriate segmented hiding technology, the security of information transmission between networks can be effectively protected, such as file transmission, printing services and so on. Devices using wireless Ethernet and WEP protocol (Wired Equivalent Protoco1) should change the default name of service set identification (SSID). Illegal users need to know the SSID name and obtain the correct encryption key to establish network connection and access the network.
SCADA server operating system. SCADA server security is an important part of SCADA system security. Simply relying on the installation of firewall and IP address segmentation hiding technology can not ensure the security and reliability of the system. An experienced hacker can often easily bypass the firewall and even use the address resolution protocol to implement ARP spoofing attack in the LAN. The primary premise for the SCADA application on the operating system to operate normally is the security of the SCADA server operating system. The vulnerability threat of operating system has increased recently. Relevant surveys show that 80% of server security problems are related to the operating system. Once viruses, worms, malicious code, spyware and rogue software invade the server and obtain the permission of the operating system administrator, their behavior is not only uncontrolled, but also can remove the traces of behavior, resulting in the inability to trace their source. At present, the operating system represented by Microsoft Windows continues to find vulnerabilities. Usually, the corresponding worm will be generated within 1-2 weeks after the vulnerability is disclosed. Weak user security awareness, careless user password selection, unauthorized user access and lax user account management will pose a threat to the security of the server operating system. Timely updating the patch file of the server operating system is an effective method to resist the latest vulnerabilities. At the same time, the default empty administrator account should be modified or even deleted.
SCADA application. Enterprises ensure the safety of applications in SCADA system. Application vulnerabilities lead to Trojans and worms that can be easily installed and attack the application system. They can be used to process data or issue instructions on the server. When the operator wants to execute an instruction or click a button, it will trigger the batch file pre implanted in the system, resulting in the deletion of all disk files or the wrong modification of the output / V status of the system. When other computers in the system use mail services, they will also be implanted with Trojan horse programs or infected with computer viruses. These Trojans and viruses invade the adjacent SCADA application server and wait for the specified time or other trigger conditions for the driver to run. Effective methods to mitigate these situations include installing anti-virus programs on computers running SCADA application software, disabling any unauthorized software installation by system administrators, and other policies and management regulations applicable to SCADA system.
SCADA policy and management. SCADA system policies and management measures involve suppliers, remote access rights and password management. SCADA system policies and regulations can greatly affect the possible security threats to the internal equipment of SCADA network. Formulating and adhering to the implementation of appropriate policies and management regulations will greatly improve the security status of SCADA system.
5 Conclusion
Based on the analysis of network security hidden dangers of Open SCADA system, this paper puts forward a security strategy of "defense circle" based on hierarchical structure. In the specific implementation process, combined with the actual situation of enterprise SCADA system characteristics, security level requirements and cost control, each layer can be optimized and reasonably configured. The "defense circle" strategy shows the characteristics of high feasibility, good prevention effect and flexible configuration. The problem that needs to be noticed is that after enterprises set up the information network, the correct management and monitoring of network equipment will become more complex. We must realize that if we only adopt purely technical solutions without close management and monitoring, the effect of safety protection will be greatly reduced. Therefore, we can consider cooperating with professional network security companies, or setting up a full-time network security engineer post in the company to carry out network security monitoring and accident prevention. This can effectively improve the performance and role of the existing information security mechanism.

 Manager Wang
Manager Wang
 OfficialAccounts
OfficialAccounts